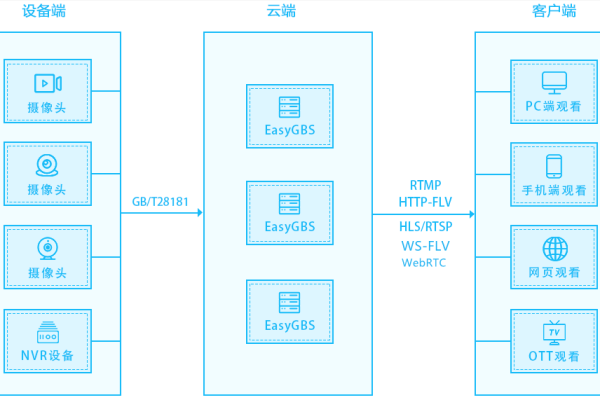
如何通过Namecheap教程为动态DNS配置主机记录?
- 行业动态
- 2024-10-10
- 3
在网络世界中,域名系统(DNS)扮演着至关重要的角色,它负责将人类可读的域名转换为机器可以理解的IP地址,对于拥有动态IP地址的用户来说,动态DNS服务是保持在线服务连续性的关键,Namecheap作为一家知名的域名注册商和网站托管服务提供商,提供了便捷的动态DNS设置功能,以下是一些如何为动态DNS设置主机记录的教程:
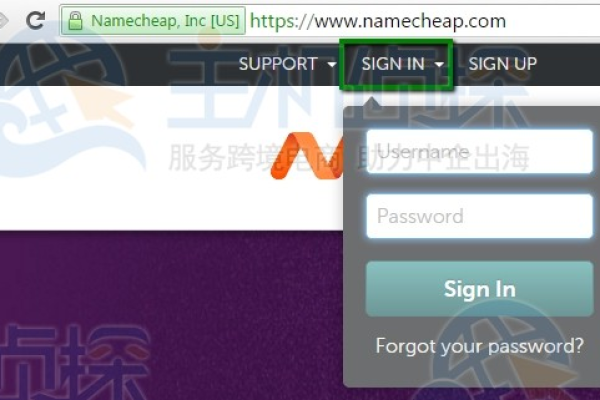
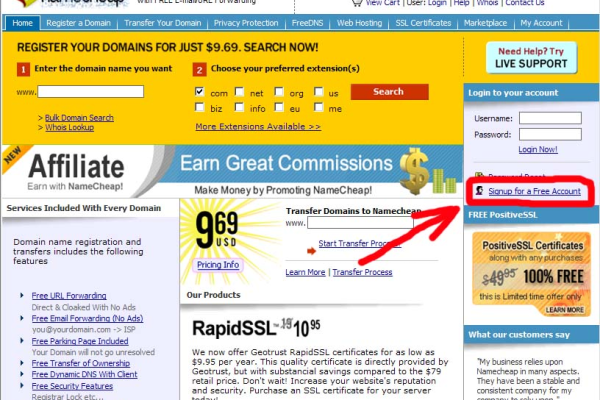
1、登录Namecheap账户:访问Namecheap官网并使用您的用户名和密码登录,如果尚未拥有账户,需要先注册一个。
2、进入域名管理界面:在控制面板中找到“Domain List”或“我的域名”,点击您想要配置动态DNS的域名旁的“Manage”按钮。
3、访问高级DNS设置:在域名管理界面中,找到并点击“Advanced DNS”选项。
4、添加A记录:在DNS设置页面,您可以添加新的记录,对于动态DNS,通常需要设置A记录,点击“Add New Record”或类似的按钮来创建新记录。
5、配置A记录:在新记录的配置中,选择记录类型为“A”,主机名通常使用@符号表示主域名,而子域名则使用www或其他前缀,在“Value”字段中,输入您的服务器IP地址。
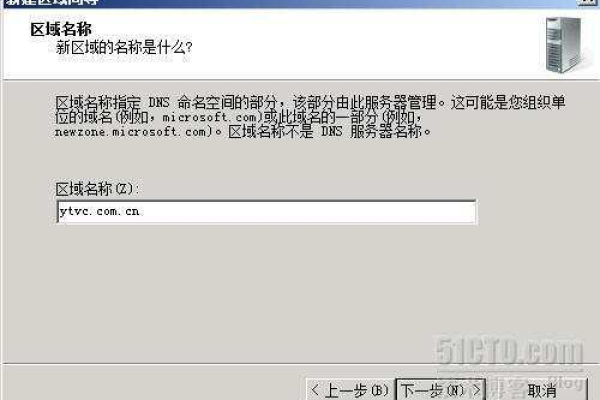
6、保存更改:完成记录的添加和编辑后,记得点击“Save Changes”或“Update Settings”按钮以保存您的配置。
7、等待DNS传播:DNS更改可能需要一些时间才能在整个互联网中传播,这通常需要几个小时到48小时不等。
8、测试DNS设置:使用命令提示符或在线工具如“ping”或“nslookup”来测试您的DNS设置是否正确。
9、更新动态DNS客户端:如果您使用的是第三方动态DNS客户端,确保它已正确配置并与您的Namecheap账户关联,这样,当您的IP地址发生变化时,客户端会自动更新DNS记录。
10、监控和维护:定期检查您的DNS设置,确保它们仍然有效,并根据需要进行更新。
相关问题与解答
1、问题一:如果我已经有一个静态IP地址,我还可以使用Namecheap的动态DNS服务吗?
解答:即使您有静态IP地址,您仍然可以使用Namecheap的动态DNS服务,动态DNS的主要优势在于能够自动更新DNS记录以反映IP地址的变化,这对于没有固定IP地址的家庭网络用户尤其有用,即使您的IP地址是静态的,使用动态DNS服务也可以简化DNS记录的管理过程。
2、问题二:Namecheap的免费DNS服务有哪些限制?
解答:Namecheap提供的免费DNS服务通常有一些限制,例如较低的查询速率限制、有限的DNS记录类型和可能的附加广告,免费服务可能不包括一些高级功能,如URL转发、电子邮件托管或更高级的DNS管理工具,对于大多数个人和小型企业用户来说,免费服务已经足够满足基本需求,对于需要更高性能或更多功能的用户,Namecheap也提供付费的DNS管理服务。
通过遵循以上步骤,用户可以有效地利用Namecheap的动态DNS服务来维护其在线服务的可用性和可靠性,无论是个人博客还是小型企业网站,正确的DNS配置都是确保网站顺畅运行的关键。
小伙伴们,上文介绍了“Namecheap教程:如何为动态DNS设置主机记录”的内容,你了解清楚吗?希望对你有所帮助,任何问题可以给我留言,让我们下期再见吧。