域名型SSL证书的年费是多少?
- 行业动态
- 2024-10-08
- 2
域名型SSL证书价格分析
不同品牌的价格对比
1、TrustAsia:
单域名(DV)SSL 证书:699元/年。
通配符SSL 证书:1999元/年。
2、Geotrust:
单域名(DV)SSL 证书:暂无具体数据。
通配符SSL 证书:7278元/年。
3、DigiCert:
单域名(DV)SSL 证书:3465元/年。

通配符SSL 证书:1500元/年。
4、阿里云:
单域名(DV)WoSign SSL 证书:238.5元/年。
通配符SSL 证书:1500元/年。
5、腾讯云:
单域名(DV)SSL 证书:560元/年。
通配符SSL 证书:2260元/年。

6、DNSPod:
单域名(DV)SSL 证书:560元/年。
通配符SSL 证书:2260元/年。
不同类型及年限的价格比较
| 类型 | 年限 | TrustAsia价格(元) | Geotrust价格(元) | DigiCert价格(元) | 阿里云价格(元) | 腾讯云价格(元) | DNSPod价格(元) |
| –| –| –| –| –| –| –|
| 单域名(DV)SSL 证书 | 1年 | 699 | | 3465 | 238.5 | 560 | 560 |
| 通配符SSL 证书 | 1年 | 1999 | 7278 | 1500 | 1500 | 2260 | 2260 |
常见问题与解答
1、为什么不同品牌的域名型SSL证书价格差异这么大?
答案:不同品牌的域名型SSL证书价格差异主要由于品牌影响力、验证流程的复杂程度和附加服务的不同,DigiCert作为老牌CA机构,其价格相对较高,而一些新兴品牌如TrustAsia则通过较低的价格吸引用户,不同品牌提供的保险赔付额度和技术支持也有所不同,这些因素都会影响最终售价。
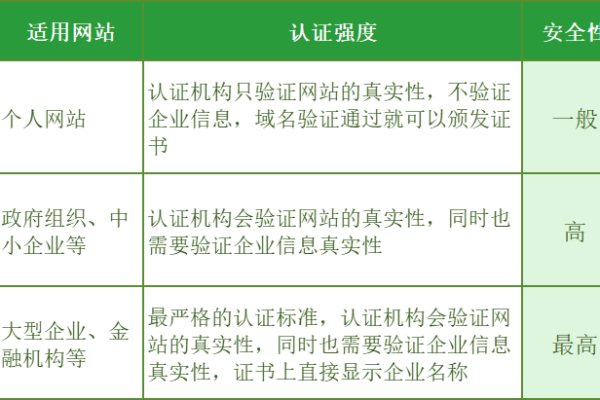
2、域名型SSL证书和企业型SSL证书有什么区别?
答案:域名型SSL证书(DV证书)主要验证域名的所有权,适合个人网站和小型企业使用,申请流程简单且价格较低,企业型SSL证书(OV证书)则需要验证企业的具体信息,包括营业执照等,提供更高的信任级别,适用于中大型企业,价格较高,增强型SSL证书(EV证书)则需要最严格的验证,包括企业身份的彻底核查,适用于金融和电子商务类网站,价格最高。
到此,以上就是小编对于“域名型SSL证书多少钱一年 域名型SSL证书价格”的问题就介绍到这了,希望介绍的几点解答对大家有用,有任何问题和不懂的,欢迎各位朋友在评论区讨论,给我留言。