如何利用phpStudy成功连接到MySQL数据库?
- 行业动态
- 2024-10-08
- 4
php,,“
phpStudy怎么连接MySQL数据库
PHPStudy是一款集成了PHP、Apache、MySQL等多个组件的本地开发环境工具,非常适合初学者和小型项目的开发,本文将详细介绍如何使用phpStudy连接MySQL数据库,包括使用命令行和图形界面工具的方法,以及如何配置环境变量以便在任意位置使用命令行连接数据库。
连接方法
1、使用MySQL命令行进行连接:
启动phpStudy,确保MySQL服务已经开启。
点击其他选项菜单,选择网站根目录。
进入PHPTutorial目录,点击MySQL文件,再点击bin文件。
在空白处右键选择“在终端中打开”。
输入mysql -uroot -p,按回车键,默认密码是root。
连接成功后,你将看到MySQL命令行提示符。
2、使用MySQL-front连接:
点击MySQL管理器,再点击MySQL-front。
如果可以直接打开,点击“打开”即可;如果需要创建用户,按照提示操作。
创建用户后,点击确定连接成功。
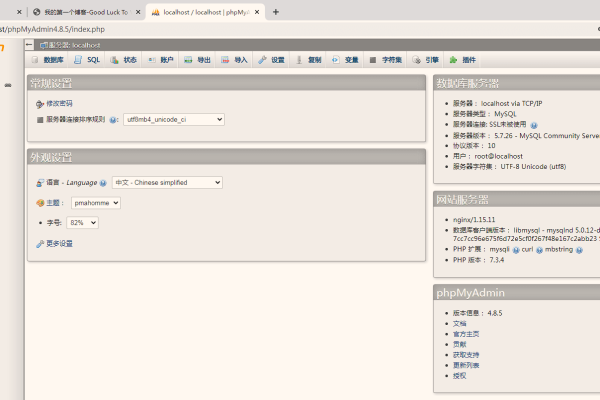
3、使用phpMyAdmin连接:
打开浏览器,输入http://localhost/phpmyadmin。
输入用户名和密码(默认都是root),点击登录。
登录成功后,你可以在这里管理你的数据库。
4、使用Navicat连接:
打开Navicat,点击连接,选择MySQL。
填入对应参数(主机地址为localhost,端口为3306,用户名和密码为root)。
点击测试连接,成功后即可使用。
配置环境
1、目的:为了能随时在任意文件位置使用cmd进入命令面板连接数据库。
2、配置操作:
复制进入bin的路径(C:phpstudy_proExtensionsMySQL5.7bin)。
右键点击此电脑,选择属性。
点击高级系统设置,再点击环境变量。
在系统变量中找到Path,点击新建,将复制的路径粘贴进去。
一路点击确定保存。
相关问题与解答
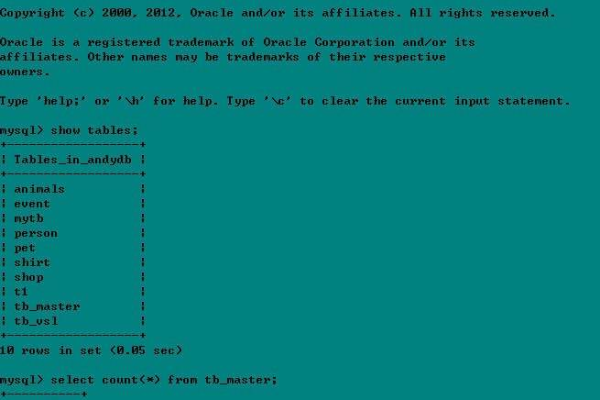
1、问题1:如何在phpStudy中升级MySQL版本?
答案:首先查看当前phpStudy中的MySQL版本,可以使用select version();命令,如果需要升级到更高版本,可以下载对应版本的MySQL,替换原有的MySQL文件夹,并重启phpStudy,具体步骤可以参考相关教程。
2、问题2:如何解决MySQL服务无法启动的问题?
答案:检查MySQL服务的端口是否被占用,尝试更换端口号,确保配置文件中的设置正确,特别是端口、用户名和密码等信息,如果问题依旧,可以尝试重新安装phpStudy或MySQL服务。
通过上述步骤,你应该能够成功在phpStudy中连接和管理MySQL数据库,如果在实际操作中遇到任何问题,可以参考官方文档或社区论坛寻求帮助,希望这篇文章对你有所帮助,祝你开发顺利!
到此,以上就是小编对于“phpStudy怎么连接MySQL数据库”的问题就介绍到这了,希望介绍的几点解答对大家有用,有任何问题和不懂的,欢迎各位朋友在评论区讨论,给我留言。