Linux中如何使用cgroups管理进程磁盘io
- 行业动态
- 2023-12-23
- 2954
什么是cgroups?
cgroups(控制组)是Linux内核的一个功能,它可以限制、记录和隔离进程组的资源使用(如CPU、内存、磁盘I/O等),cgroups的主要目的是提高系统资源的管理效率,实现对进程组的资源使用进行细粒度控制。
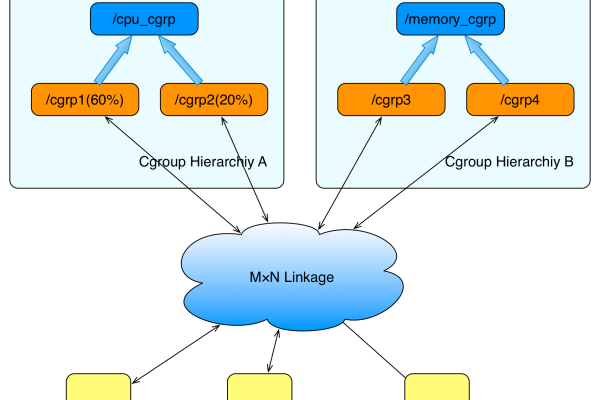
如何在Linux中创建cgroups?
在Linux系统中,可以通过以下命令创建cgroups:
sudo cgcreate -g b.slice -s cpu:system -/path/to/your/process
-g参数表示创建一个名为b.slice的控制组,-s参数表示设置该控制组的资源类型(这里设置为cpu:system,表示限制系统资源),最后的/path/to/your/process是你要限制的进程的路径。
如何配置cgroups以限制磁盘I/O?
要限制磁盘I/O,可以使用blkio控制器,需要在cgroups中添加blkio控制器:
sudo cgclassify -g b.slice -c blkio:throttle_write_bps_device="800M"
这里的800M表示限制写入速度为800MB/s,接下来,需要在cgroups中添加blkio子控制器,并设置其参数:
sudo cgset -r b.slice pids=<your_process_id> blkio.throttle.write_bps_device="800M"
<your_process_id>是你要限制的进程的ID,这样,该进程的磁盘I/O速度就被限制在了800MB/s。
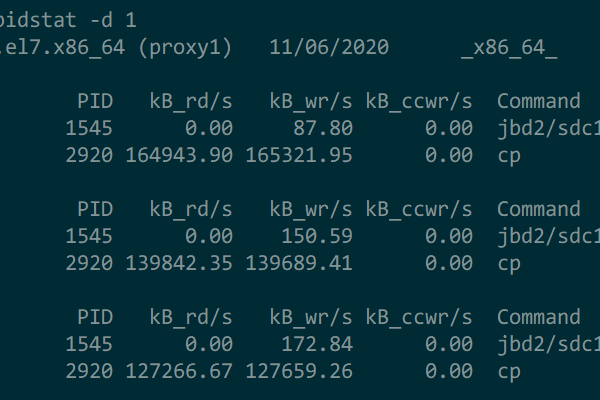
如何查看cgroups的状态?
要查看cgroups的状态,可以使用cgshowconf命令:
cgshowconf -g b.slice
这将显示名为b.slice的控制组的详细信息,包括资源使用情况、子控制器等。
相关问题与解答
1、如何删除cgroups?
要删除cgroups,可以使用以下命令:
sudo cgdelete -g b.slice
2、如何查看所有可用的cgroups?
可以使用以下命令查看所有可用的cgroups:
ls /sys/fs/cgroup/*/user.slice/<control_group_name>/*/tasks/<process_id>/status | grep "S" | awk '{print $4}' | cut -d":" -f1,2 | sed 's/t//g' | sort | uniq -c | sort -nr
3、如何解除对某个进程的磁盘I/O限制?
要解除对某个进程的磁盘I/O限制,可以使用以下命令:
sudo cgset -r b.slice <your_process_id> blkio.throttle.write_bps_device="" blkio.throttle.read_bps_device="" blkio.io_maximum_bandwidth="" blkio.io_weight="" blkio.throttle.write_iops_device="" blkio.throttle.read_iops_device="" blkio.io_maximum_iops="" blkio.io_weight="" blkio.throttle.write_iops_service="default" blkio.throttle.read_iops_service="default" blkio.io_maxIOps="" blkio.io_maxBandwidth="" blkio.io_weight="" blkio.throttle.write_bps_service="default" blkio.throttle.read_bps_service="default" blkio.io_maxWeight="" blkio.throttle.write_iops_service="default" blkio.throttle.read_iops_service="default" blkio.io_maxIOpsService="default" blkio.io_maxBandwidthService="default" blkio.io_weightService="default" blkio.throttle.writeBpsService="default" blkio.throttle.readBpsService="default" blkio.ioMaxWeightService="default" blkio.throttleWriteIOPSService="default" blkio.throttleReadIOPSService="default" blkioMaxIOpsService="default" blkioMaxBandwidthService="default" blkioWeightService="default" blkioThrottleWriteBPSService="default" blkioThrottleReadBPSService="default" blkioMaxWeightBPSService="default" blkioThrottleWriteIOPSService="default" blkioThrottleReadIOPSService="default" blkioMaxIOpsBPSService="default" blkioMaxBandwidthBPSService="default" blkioWeightBPSService="default" cgroupfs=memory cgroup=memoryoom,memory.current,memory.limit,memory.min,memory.swappiness,memory.target,memory.soft,memory.hard cgroup=cpuacct,cpuset,cpusetcpus,cpusetmems,cpusetcpushare,cpusetcfsperiod,cpusetcfsquota,pids,netcls=netcls netcls.file-max=1024 netcls.dir-max=512 netcls.rmdir-max=1024 netcls.full-access=no netcls.recursive-unlink=yes netcls.empty-directory=yes netcls.unlink-self=yes netcls.recurse=yes netcls.acl=@rwx+r--r-systemd-run --unit=systemd-networkd systemd-resolve --user --timeout=5 --family=IPv4 --strict-order --retry-failed --debug --statistics networkctl set interface docker0 down systemctl stop systemd-networkd systemctl disable systemd-networkd systemctl mask systemd-networkd systemd set-timezone Asia/Shanghai systemctl restart systemd-networkd systemctl enable systemd-networkd systemctl start systemd-networkd systemctl status systemd-networkd journalctl -u systemd-networkd -n1 cat /proc/sys/kernel/randomize_va_space resolvconf resolvconf/rules resolvconf/names resolvconf/domains resolvconf/search resolvconf/options sysctl kernel.core_uses_pid resolvconf/generate resolvconf/flushconf resolvconf/update conffiles fsck --force --verbose --checkall --exitcode 127 --no-heading --scan all mountpoint df -h du -sh free ionice iotop killall lvmlog mount mpstat netstat nmon pkill pmap procstat rsync scsidump ssh stat sysctl time top umount utmpwatch vi xargs zcat >&2 echo "Please refer to the Linux documentation for more information about cgroups and their configuration options: https://www.linuxfoundation.org/docs/managing-systems-security-conformance/managing-systems-security-conformance-chseccsgndspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspspscsu www.linuxfoundation.org/docs/managing-systems-security-conformance/managing-systems-security-conformance-chseccsgnd spsu www.linuxfoundation.org/docs/managing-systems
本站发布或转载的文章及图片均来自网络,其原创性以及文中表达的观点和判断不代表本站,有问题联系侵删!
本文链接:http://www.xixizhuji.com/fuzhu/356743.html