如何实现远程连接到Windows VPS?
- 行业动态
- 2024-10-07
- 2
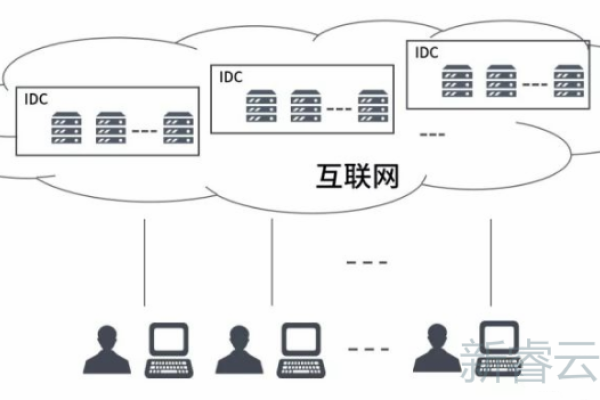
Windows VPS怎么远程连接 Windows VPS远程连接教程
一、Windows系统自带的远程桌面连接工具使用指南
1、启动远程桌面连接:
打开“开始”菜单,选择“所有程序”,然后找到并点击“附件”下的“远程桌面连接”。
或者,按下Win + R键,输入mstsc命令,再按回车键。
2、输入VPS服务器信息:
在弹出的“远程桌面连接”窗口中,输入您的VPS服务器的IP地址和端口号(如果使用的是非标准端口)。192.168.1.191:3389。
如果是第一次连接,可以点击左下角的“选项”按钮,提前填好用户名等信息,并保存凭据以便下次快速连接。
3、进行连接并处理安全提示:
点击“连接”后,会弹出一个窗口要求输入用户名和密码,输入正确的凭证后,点击“确定”。
如果出现SSL证书警告,通常可以忽略此警告,勾选“不再询问我是否连接到此计算机”的选项,然后继续。
4、成功登录并操作:
完成上述步骤后,您应该能看到VPS服务器的桌面环境,此时您可以像操作本地电脑一样进行各种操作了。
使用IIS7远程桌面管理工具连接VPS
1、下载并安装IIS7远程桌面管理工具:
从可靠的来源下载IIS7远程桌面管理工具的安装包。
2、添加VPS服务器信息:
打开IIS7远程桌面管理工具,点击“添加机器”。
输入服务器的IP地址、端口号(默认为3389,除非已更改)、账号和密码。
3、连接到VPS服务器:
添加完服务器信息后,双击列表中的服务器即可开始远程连接。
4、批量管理(可选):
如果需要管理多台VPS服务器,可以使用IIS7的全选功能,一键打开所有已添加的服务器。
三、从Mac OS连接到Windows VPS
1、下载Microsoft Remote Desktop应用:
打开Mac App Store,搜索并下载Microsoft Remote Desktop应用。
2、创建新的远程桌面连接:
打开应用后,点击“新建”按钮。

输入PC名称(即VPS的IP地址),以及用户名和密码。
3、保存并连接:
填写完信息后,按左上角的红色X按钮保存连接设置。
返回主界面,选中刚创建的连接,点击“开始”按钮进行连接。
4、处理安全提示:
如果遇到证书警告,选择信任并继续连接。
5、完成连接并操作:
连接成功后,您将看到VPS服务器的桌面环境,可以开始进行操作了。
常见问题与解答
1、为什么我无法连接到VPS?
确保您输入的IP地址、端口号、用户名和密码都是正确的。
检查VPS服务器是否已启动,并且远程桌面服务是开启状态。
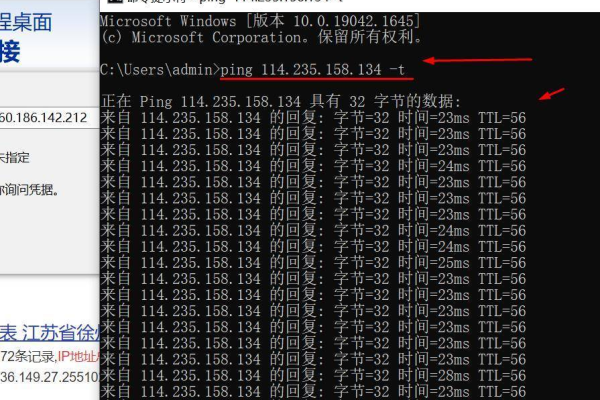
确认网络连接正常,没有防火墙或安全组规则阻止连接。
2、连接时出现“发生身份验证错误”怎么办?
请重新检查您输入的用户名和密码是否正确。
尝试重置VPS服务器上的远程桌面用户密码,然后再试一次。
3、如何提高远程连接的安全性?
建议修改默认的远程桌面端口(如从3389改为其他不常用的端口)。
使用强密码,并定期更换。
考虑使用网络传输层或SSH隧道来加密远程连接的数据流。
以上就是关于“Windows VPS怎么远程连接 Windows VPS远程连接教程”的问题,朋友们可以点击主页了解更多内容,希望可以够帮助大家!