实现安全可靠的Oracle互联网访问
- 行业动态
- 2024-04-26
- 4377
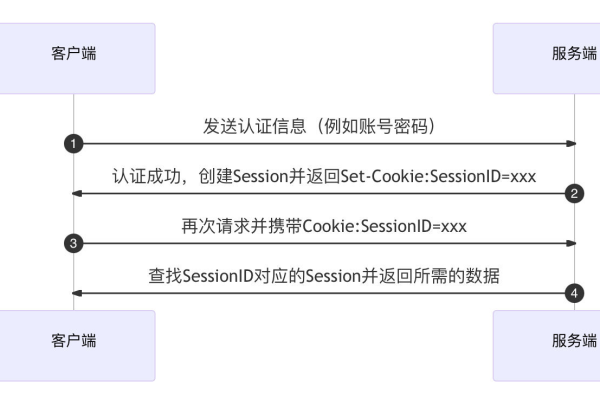
Oracle数据库作为企业级的关系型数据库管理系统,广泛应用于各种业务场景,随着互联网技术的发展,如何实现安全可靠的Oracle互联网访问成为了一个重要的问题,本文将详细介绍如何实现安全可靠的Oracle互联网访问,包括技术原理、操作步骤和注意事项。
技术原理
1、SSL加密:SSL(Secure Sockets Layer)是一种网络安全协议,用于在客户端和服务器之间建立安全通道,通过SSL加密,可以保证数据在传输过程中的安全性和完整性。
2、IP白名单:IP白名单是一种访问控制策略,只允许特定的IP地址或IP地址段访问数据库,通过设置IP白名单,可以有效防止非规访问和攻击。
3、用户名和密码验证:在用户访问数据库时,需要提供有效的用户名和密码进行验证,只有通过验证的用户才能访问数据库,从而保证数据的安全性。
4、数据库审计:数据库审计是指对数据库的操作进行记录和分析,以便发现和防止潜在的安全问题,通过数据库审计,可以追踪和分析用户的操作行为,及时发现异常情况。
操作步骤
1、配置SSL加密
(1)生成密钥库文件:使用Oracle自带的keytool工具生成密钥库文件,命令如下:
keytool genkey alias oracle keyalg RSA keystore keystore.jks storepass password validity 3650
alias oracle表示密钥库的别名,keyalg RSA表示密钥算法为RSA,keystore keystore.jks表示密钥库文件的名称,storepass password表示密钥库的密码,validity 3650表示密钥的有效期为3650天。
(2)配置监听器:编辑Oracle监听器的配置文件(listener.ora),添加以下内容:
SID_LIST_LISTENER =
(SID_LIST =
(SID_DESC =
(SID_NAME = ORCL)
(ORACLE_HOME = /u01/app/oracle/product/11.2.0/dbhome_1)
(PROGRAM = extproc)
)
(SID_DESC =
(GLOBAL_DBNAME = orcl)
(ORACLE_HOME = /u01/app/oracle/product/11.2.0/dbhome_1)
(SID_NAME = ORCL)
)
)
ORCL是数据库实例名,/u01/app/oracle/product/11.2.0/dbhome_1是Oracle安装路径。
(3)配置tnsnames.ora文件:编辑tnsnames.ora文件,添加以下内容:
ORCL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = your_host)(PORT = your_port))
)
(CONNECT_DATA =
(SERVICE_NAME = ORCL)
)
)
your_host是数据库服务器的主机名或IP地址,your_port是监听器的端口号。
2、配置IP白名单
(1)登录数据库服务器,打开iptables配置文件:
sudo vi /etc/sysconfig/iptables
(2)添加以下内容:
A INPUT p tcp dport your_port s your_ip m state state NEW,ESTABLISHED j ACCEPT
your_port是监听器的端口号,your_ip是允许访问的客户端IP地址。
(3)保存并退出,然后重启iptables服务:
sudo service iptables restart
3、配置用户名和密码验证
(1)登录数据库服务器,打开sqlnet.ora配置文件:
sudo vi /etc/oracle/sqlnet.ora
(2)添加以下内容:
SQLNET.AUTHENTICATION_SERVICES = (NONE)
(3)保存并退出,然后修改监听器配置文件(listener.ora),添加以下内容:
DIAG_ADR_ENABLED=OFF
4、开启数据库审计功能
(1)以SYSDBA身份登录数据库:
conn / as sysdba;
(2)启用审计策略:
audit all; 审计所有对象和操作类型,可以根据需要进行调整,audit table by access; audit select by column; audit update by row; audit delete by row; audit insert by statement; audit drop by statement; audit create by statement; audit alter by statement; audit index by access; audit trigger by statement; audit privilege by usage; audit role by usage; audit schema by statement; audit sequence by access; audit synonym by access; audit view by access; audit materialized view by access; audit procedure by statement; audit package by statement; audit type by usage; audit directory by access; audit java class by name call return; audit java method by name call return object; audit java system event by name call return object; audit java user defined event by name call return object; audit datatype by usage; audit operator by usage; audit operator by type; audit cluster by operation type; audit cluster by table access; audit cluster by index access; audit cluster by bitmap scan access; audit cluster by hash join access; audit cluster by nested loops join access; audit cluster by sort access; audit cluster by streams agg function access; audit cluster by parallel query server job access; audit cluster by db link access; audit cluster by external job call access; audit cluster by queue message access; audit cluster by clob write access; audit cluster by lob write access; audit cluster by lob read access; audit cluster by collection write access; audit cluster by collection element write access; audit cluster by collection element delete access; audit cluster by collection fetch operation access; audit cluster by collection bulk collect operation access; audit cluster by collection bulk modify operation access; audit cluster by array write access; audit cluster by array fetch operation access; audit cluster by jdbc call return object access; audit cluster by jdbc stored procedure call return object access; audit cluster by jdbc prepared statement call return object access; audit cluster by jdbc call parameter access; audit cluster by jdbc update batch return status access; audit cluster by jdbc update batch nonbatchable exception access; audit cluster by jdbc update batch update counts access; audit cluster by jdbc update batch other exceptions access; audit cluster by jdbc call escape string access; audit cluster by jdbc call time zone id access; audit cluster of utl file read and write operations on files in the database file system or removable media accessible to the instance using the standard UTL file APIs for reading and writing text files and binary files in ASCII and binary formats. 根据实际情况选择需要审计的策略。
本站发布或转载的文章及图片均来自网络,其原创性以及文中表达的观点和判断不代表本站,有问题联系侵删!
本文链接:http://www.xixizhuji.com/fuzhu/246284.html