揭秘IIS7.5,ApplicationPoolIdentity究竟是什么?
- 行业动态
- 2024-09-01
- 4552
ApplicationPoolIdentity是IIS7.5中的一种新型身份,它为应用程序池提供了一种运行在最小权限下的隔离环境。这种身份主要用于提高安全性,防止反面软件或者攻击者获取更高的系统权限。
IIS 7.5 introduced a significant change in the way that application pools could run with the introduction of the ApplicationPoolIdentity. This feature, available only on Windows 7, Windows 2008 SP2, and Windows 2008 R2, provided a new identity for application pools that was more secure and isolated than traditional methods. In this article, we will delve into what ApplicationPoolIdentity is, how it works, and its benefits compared to other identity options like LocalService, LocalSystem, and NetworkService.

ApplicationPoolIdentity is a special identity that IIS creates automatically when an application pool is instantiated. Unlike the traditional builtin accounts, ApplicationPoolIdentity does not run as a predefined user or group in the operating system; instead, it runs under a dynamically created, unique security context called an Application Pool SID (Security Identifier).
The Application Pool SID is generated by IIS at runtime and is not a real user account; it cannot be used to log into a system or be assigned rights to files and folders directly. The beauty of this approach lies in its isolation and least privilege principle: the identity has only the permissions explicitly granted to it, reducing the attack surface should a website be compromised.
Comparing ApplicationPoolIdentity to the older models like LocalService, LocalSystem, and NetworkService brings several advantages into perspective. The LocalService and LocalSystem accounts have broad permissions across the system, often more than is necessary for web applications. NetworkService, while less privileged than LocalSystem, still retains broader access rights than needed in many cases.
The following table summarizes the differences between these identities:
| Identity Type | Description | Privilege Level | Isolation |
| LocalSystem | Highly privileged; acts as the local system | Highest | Least |
| LocalService | Less privileged; acts on behalf of the local system | High | Low |
| NetworkService | Runs in the context of the network service account | Medium | Medium |
| ApplicationPoolIdentity | Runs under a unique SID per application pool | Least privilege required | Most |
ApplicationPoolIdentity’s unique SID ensures that even if multiple application pools are running under this identity, they remain isolated from each other. This means that if one pool is compromised, it doesn’t inherently affect the security of other pools running under ApplicationPoolIdentity.
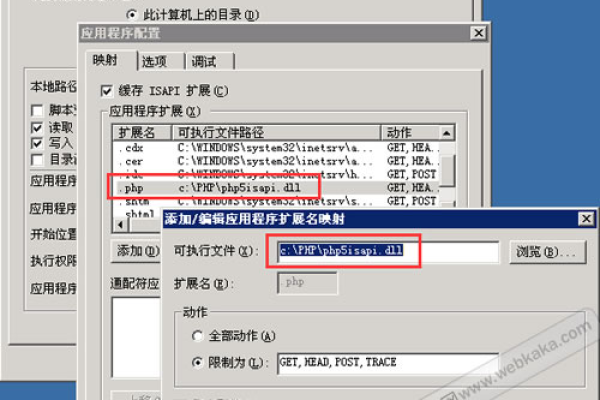
One crucial aspect to consider when using ApplicationPoolIdentity is the handling of file system permissions. Since ApplicationPoolIdentity doesn’t correspond to a real user account, granting permissions can be tricky. One common approach is to use the "IIS AppPoolAppPoolName" syntax when setting permissions in Windows Explorer or through command line tools.
Another consideration is network resource access. Since ApplicationPoolIdentity lacks a real network profile, any attempts to access network resources require different authentication mechanisms such as Kerberos delegation or using a service account with appropriate network rights.
In conclusion, ApplicationPoolIdentity in IIS 7.5 offers a more secure and isolated environment for running web applications. Its use of dynamic SIDs ensures that each application pool operates with the least set of privileges necessary, reducing the potential impact should security breaches occur. While it requires a bit more setup for file system and network resource access, the increased security makes it a recommended approach for hosting sensitive applications.
FAQs
Q1: How do I assign file permissions to ApplicationPoolIdentity?
A1: To assign file permissions to ApplicationPoolIdentity, use the "IIS AppPoolAppPoolName" syntax in the security properties of the file or folder. This method associates the permission with the application pool’s virtual identity.
Q2: Can ApplicationPoolIdentity access network resources?
A2: By default, ApplicationPoolIdentity cannot access network resources because it doesn’t have a network profile. To enable network resource access, you need to implement Kerberos delegation or use a service account with appropriate network permissions.
本站发布或转载的文章及图片均来自网络,其原创性以及文中表达的观点和判断不代表本站,有问题联系侵删!
本文链接:https://www.xixizhuji.com/fuzhu/150810.html